hannah floeter professor mary hays rhet 105 march 8, 2016 rapid development of cyber warfare sparks international debate workin
Hannah Floeter
Professor Mary Hays
RHET 105
March 8, 2016
Rapid Development of Cyber Warfare Sparks International Debate
Working Thesis: Cyber warfare has development so rapidly that
international law has not been able to keep up with it.
Dev, Priyanka R. ""Use of Force" and "Armed Attack" Thresholds in
Cyber Conflict: The Looming Definitional Gaps and the Growing Need for
Formal U.N. Response." Texas International Law Journal 50.2 (2015):
379-99. EBSCOhost. Web. 28 Feb. 2016.
This article describes the challenges faced by the international law
over cyber warfare and the dangers it entails. The author states, “As
the dangers of cyber actions evolve in the wake of technological
developments, so too should the way States and organizations apply
traditional law of armed conflict (LOAC) principles to cyber actions.”
The topics discussed include existing laws of war in the context of
information security, the Iranian hackers attack, and the need to
reform traditional law of armed conflict. The stress is being placed
on reforming the laws of combat to also cover the laws of cyber war.
This source is an academic journal, and therefore is a trustworthy and
scholarly source. This source is also only a year old, so it is very
current. Although it is a good source, most of the information doesn’t
help support my thesis. I will probably only end up using the part
about the reformation of the laws in combat warfare.
Dombrowski, Peter, and Chris C. Demchak. "CYBER WAR, CYBERED CONFLICT,
AND THE MARITIME DOMAIN." Naval War College Review 67.2 (2014): 71-97.
EBSCOhost. Web. 28 Feb. 2016.
This article discusses the connection between cyber war to the U.S.
Navy and maritime strategy. It talks about the U.S. CyberCommand and
the U.S. Department of Defense. They have found ways to use cyber
warfare to help with precision targeting in naval warfare. It also
discusses the complexity of not knowing when an attack will occur. The
author says that governments have started to use trends to predict
attacks.
Since this source is an academic journal, it is scholarly and
trustworthy. The authors are affiliated with the Naval War College as
a professors, so they are reliable. This source is only a couple years
old so it recent news. I can use this source to relate it to my thesis
by comparing the navy before the cyber warfare technology and after
the technology.
Engelhardt, Tom. The United States of Fear. Chicago: Haymarket, 2011.
Print.
The argues that the costs of war under the Bush and Obama
administrations have increased the US deficit by a large amount. He
states that the United States is declining because of the unreasonably
massive military budget. He states that America is no longer the
global supremacy. Engelhardt gives solutions to the problems of the US
overspending on the military and says that America needs to back out
of global issues.
This book was published in 2011, so it is fairly recent. The author is
well respected, but his book is very biased. It will be important to
understand the difference between facts and his opinion.
Friedman, Jonah. "Cyber Weapons vs. Nuclear Weapons." Center for
Strategic and International Studies. N.p., 26 July 2011. Web. 28 Feb.
2016.
This article compares the use of nuclear weapons with cyber warfare.
The states that nuclear weapons were quickly developed and similarly
did not have many laws to limit its use when it first was being used.
The author also states that developing useful strategies for the two
in their early stages was quite challenging. She says that we have
learned to handle nuclear weapons so our society will also be able to
manage cyber warfare.
This article is a blog from a website. The website seems very
credible, but the article was written on a blog linked to the website.
This source may not be as credible, so I so be careful when using it.
The article is also five years old, so it may be a little out of date.
Kirsch, Cassandra M. "Science Fiction No More: Cyber Warfare And The
United States." Denver Journal of International Law & Policy. 40.4
(2012): 620-47. EBSCOhost. Web. 28 Feb. 2016.
The article states that cyber warfare has been damaging to computer
networks around the world. Government officials from around the world
have called for the creation of a Geneva Convention equivalent for
cyber warfare. There has been disagreement in the classification of
cyber activities. Previous cyber espionage was outside of the reach of
international law, but it is now used to disable state
infrastructures. Before cyber war, wars had defined groups, but now
the Internet allows for anonymity.
This article is in an academic journal, but it has not been peer
reviewed. THe author is also the Executive Director of the University
of Denver Privacy Foundation, which means she knows about the privacy
and security of the internet. It was also written a couple of years
ago, so it is very recent.
Patterson, Ryan. "SILENCING THE CALL TO ARMS: A SHIFT AWAY FROM CYBER
ATTACKS AS WARFARE." Loyola of Los Angeles Law Review48.3 (2015):
969-1015. EBSCOhost. Web. 28 Feb. 2016.
This academic journal describes the risks of cyberspace. The author
states that cyber attacks have increased frequently and it has been
called the newest domain of warfare. He suggests that the existing
laws of war ignore the fundamental problems between cyber attacks and
combat attacks. The author argues that prosecuting cyber crimes,
seeking reparations and enhancing security, can stop cyber attacks
without treating cyber attacks as cyber warfare. The article argues
the categorization of cyber warfare under the umbrella of warfare is
not necessary.
This source is an academic journal, so this source is credible. The
article has not been peer reviewed. This article was also written
recently, so it argues current issues. This source is against my
thesis, so I will need to think of a rebutal.
Poirier, William J., and James Lotspeich. "Air Force Cyber Warfare."
Air & Space Power Journal 27.5 (2013): 73-97. EBSCOhost. Web. 28 Feb.
2016.
This article discusses the cyber warfare in the U.S. Air Force that
can be used in the military. The capability of the Air Force in
cyberspace is very important, since all planes are connected to the
internet and can easily be hacked. Since warfare in the cyberspace is
still underdeveloped, it has its weaknesses. Over time commanders will
learn how to best utilize the cyber forces through effective
development of weapon systems.
This source is an academic journal, and therefore it is a reliable
source. This source has not been peer reviewed, so it may not be as
trustworthy. This source is only three years old, so it’s still pretty
recent. I can use this source to show how the Air Force has evolved by
using cyber space.
Pool, Phillip. "War of the Cyber World: The Law of Cyber Warfare."International
Lawyer 47.2 (2013): 299-323. EBSCOhost. Web. 28 Feb. 2016.
This article describes the rapid advancements in technology and the
increase in cyber attacks. Since this is an up and coming type of
warfare, here are not many international laws stating the framework to
govern. This type of warfare is shaping the formation of international
law. The article also describes the current “weapons” that hackers are
using to infiltrate the cyber world. Threats to nations’ security has
become more serious, and the author proposes ways that some of these
problems can be fixed
This article would be a good source to use in my paper because it is
an academic journal, which means it is reliable and scholarly. This
journal has not been peer reviewed, which means this information has
not be checked by another scholar. The article is only three years old
which is new, since cyber warfare has only been around for about 20
years.
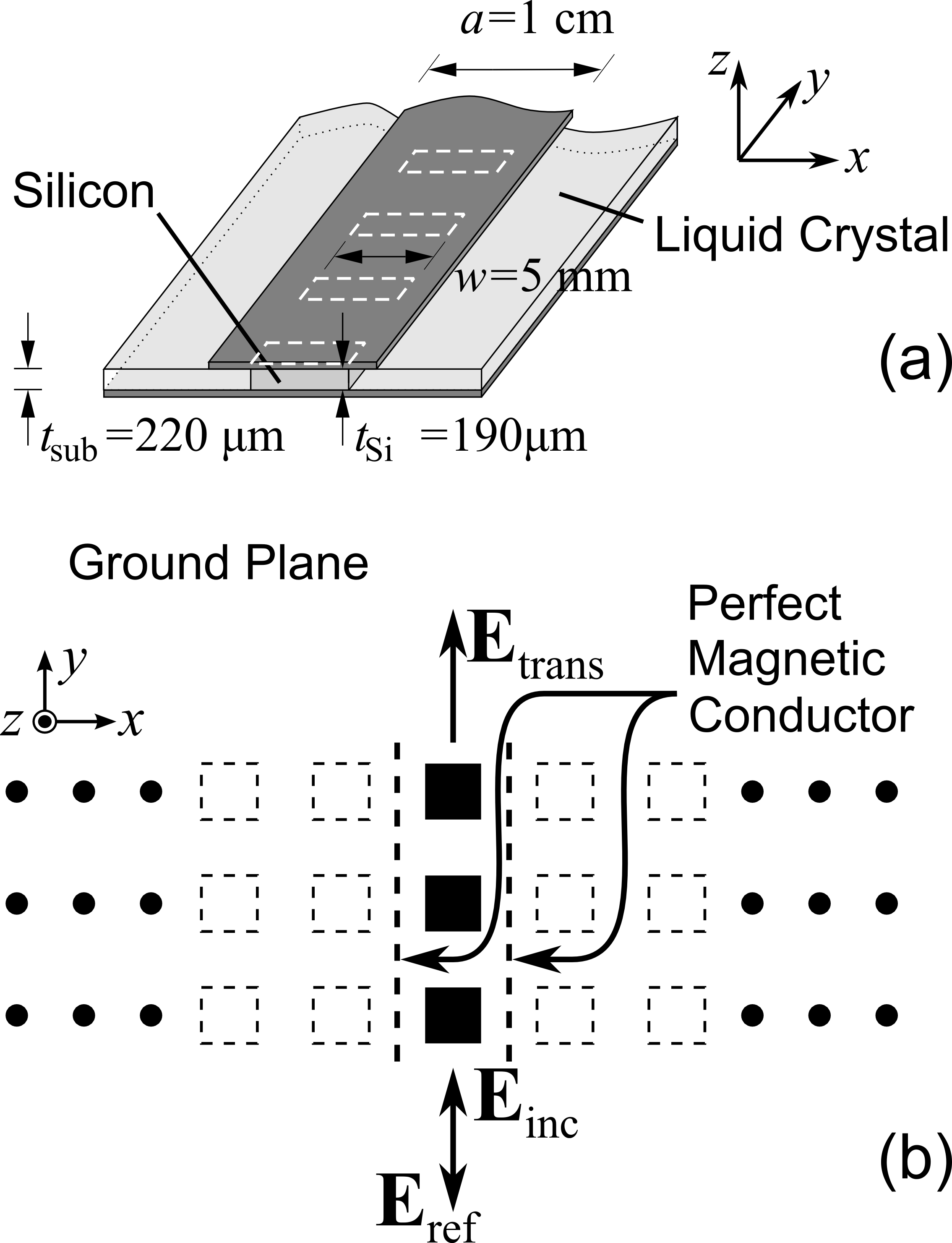 SCHAUB & OLIVER “A LIQUID CRYSTALBASED DYNAMICALLY TUNABLE PHOTONIC
SCHAUB & OLIVER “A LIQUID CRYSTALBASED DYNAMICALLY TUNABLE PHOTONIC INFORME DE AUDITORIA EXPRESS NO 2 PLAN ANTICORRUPCION Y
INFORME DE AUDITORIA EXPRESS NO 2 PLAN ANTICORRUPCION Y CAPITULO I – ORGANIZACIÓN DE LA COMPETICIÓN ARTÍCULO 1
CAPITULO I – ORGANIZACIÓN DE LA COMPETICIÓN ARTÍCULO 1 DISTANCIA DE UN PUNTO A UNA RECTA SEAN
DISTANCIA DE UN PUNTO A UNA RECTA SEAN OPTIMIZING THE PLANAR STRUCTURE OF (111) AUCOAU TRILAYERS
OPTIMIZING THE PLANAR STRUCTURE OF (111) AUCOAU TRILAYERS  THÔNG TƯ HƯỚNG DẪN XÁC ĐỊNH HỆ SỐ ĐIỀU
THÔNG TƯ HƯỚNG DẪN XÁC ĐỊNH HỆ SỐ ĐIỀU 2 MICHIGAN TEST FOR TEACHER CERTIFICATION CONTENT ADVISORY COMMITTEE
2 MICHIGAN TEST FOR TEACHER CERTIFICATION CONTENT ADVISORY COMMITTEE MOKINIO VARDAS PAVARDĖ KLASĖ UŽSIENIO (RUSŲ) KALBA KLAUSYMO
MOKINIO VARDAS PAVARDĖ KLASĖ UŽSIENIO (RUSŲ) KALBA KLAUSYMO OBTAINING APPROVAL FOR A SURVEY OF US ARMY PERSONNEL
OBTAINING APPROVAL FOR A SURVEY OF US ARMY PERSONNEL