polk county local government internet and electronic mail acceptable use policy purpose the purpose of this policy is to establish gu
Polk County Local Government
Internet and Electronic Mail Acceptable Use Policy
Purpose
The purpose of this policy is to establish guidelines and minimum
requirements governing the acceptable use of County-provided Internet
Access, electronic mail (e-mail) services. By establishing and
maintaining compliance with this policy, risks and costs to the County
can be minimized while the valuable potential of these communication
tools can be realized, for the benefit of the County and its citizens.
Objectives
The objectives of this policy are to:
1.
Ensure that the use of County provided Internet Access, e-mail
services are related to, or for the benefit of, county government;
2.
Define appropriate personal usage of County provided Internet
Access and E-mail services;
3.
Inform users that electronic messages and documents are subject to
the same laws, regulations, policies, and other requirements as
information communicated in other written formats;
4.
Minimize disruptions to county government activities from
inappropriate use of County provided Internet access and/or email.
5.
Provide users with guidelines describing their personal
responsibilities regarding confidentiality, privacy, and
acceptable use of County provided Internet access and email
services as defined by this policy; and
6.
Obtain signatures from each employee stating their agreement to
this policy. The original will be held in the employee’s personnel
record in the Manager’s office. Department Heads will also be
provided a copy.
Scope
This policy applies to all full and part-time employees, temporaries,
contractors, volunteers, and other individuals who are provided
Internet access and/or e-mail services (hereinafter referred to as
“users”). Others may be provided Internet access and email services as
necessary for their business purpose with Polk County (hereafter
referred to as “The County’), provided they abide by all applicable
rules in this policy.
Policy
It is the policy of the County Of Polk to provide technological
resources to its employees to enhance their ability to perform their
job and to provide a higher level of service to all citizens. To this
end, the County will provide guidelines for the use of such technology
and train its employees in their proper usage. The County will also
require responsible usage of these resources and hold users
accountable for inappropriate use.
Background
E-mail is an efficient and timely communication tool that can be used
to accomplish government functions and conduct the County’s business
within its organization, with other governmental agencies, with
business partners, and with the public. Email can help county agencies
and departments improve the way the conduct business by providing a
quick and cost effective means to create, transmit, and respond to
messages and documents electronically. Well designed and properly
managed e-mail systems expedite business communications, reduce
paperwork and automate routine office tasks thereby increasing
productivity and reducing costs. Daily tasks are accomplished more
rapidly as individuals use e-mail services for sending and receiving
texts as well as avoiding telephone tag.
Many of the same benefits can be accorded to the Internet or the World
Wide Web. The resources are innumerable. Access to state and federal
agencies, other counties, and their agencies along with vendors and
businesses prove invaluable on a daily basis.
As with any County-provided resource, the use of the internet and
email services, should be dedicated to legitimate county business and
is governed by rules of conduct similar to those applicable to the use
of other information technology resources. Use of the internet and
e-mail service is a privilege, which imposes certain responsibilities
and obligations on users and is subject to county government policies
and local, state, and federal laws.
Definitions
E-mail – Any mail generated and transferred by electronic means. For
our purposes we are defining email as both web-mail and workstation
residing mail.
Internet Access – Access to the internet granted to users of the Polk
County Local Government Network.
Responsibilities
Employees who are provided with Internet access and e-mail service are
required to use these resources responsibly. This policy defines
responsibilities of those who use these services on a daily basis.
Information Technology Department
The Information Technology Department is responsible for the
administration of email services and providing access to the internet.
This shall include maintenance of the servers and network that allows
these services to take place, installation and updates of the email
applications and web browsers, and training in the proper use of the
email application. This department shall also provide user training of
policy issues, emphasizing acceptable and unacceptable users and
respond to questions of interpretation. This department shall be
responsible for on going review and maintenance of this policy as
required by changes in local, state, and federal law and as necessary
for local considerations. Major policy changes will be developed in
consultation with the County Manager, County Attorney, and department
heads. This department will also monitor performance and security
issues on an on-going basis.
Department Head
It is the responsibility of the Department head to support and
administer this policy and to ensure employee knowledge of and
compliance with the principles outlined herein, ensuring they are
scheduled for and receive training. Department heads may also consider
providing additional restrictions and guidelines regarding the use of
email and internet access. Department heads should be aware of
productivity issues that may arise from the overuse/misuse of email
and web surfing.
User
It is the responsibility of each user to understand this policy and
use the County provided resources in an acceptable manner. Email is
not private communication. All information transmitted via the
County’s Internet/email systems are the property of the County and are
subject to inspection by county officials. Disclosure may occur
inadvertently when email is forwarded or directed to the wrong
recipient or printed to a common area where others can read them.
Because of the various security, legal, and productivity issues
referenced in this policy, each user has the following
responsibilities;
1.
All employees must comply with this policy. Users are expected to
understand this acceptable use policy (AUP) and acceptable and
unacceptable uses in general. The burden of responsibility is on
the user to inquire as to the proper use of the Internet and
email.
2.
The content of anything exchanged (sent and/or received) via email
communications must be appropriate and consistent with county
personnel and/or agency policy, subject to the same restrictions
as any other correspondence.
3.
Email communications, if allowed to accumulate on a server, can
quickly consume the server’s disk space and cause system problems.
Although deletion of unnecessary email communications is
encouraged, users should refer to an approved retention schedule
for proper procedure regarding disposition of email
communications.
4.
Comply with all applicable federal, state, and local laws and
ordinances.
5.
Comply with county and department/agency policies, procedures, and
standards.
6.
Be courteous and follow accepted standards of etiquette.
7.
Respect and protect others’ privacy and confidentiality.
8.
Be responsible f or the use of the Internet and their email
accounts.
9.
Use information technology resources efficiently and productively.
Users should remember that existing and evolving rules, regulations,
and guidelines on ethical behavior of government employees and
appropriate use of government resources apply to the use of electronic
communications systems supplied by the County of Polk.
Personal Use
Personal use of County provided Internet access and email services are
allowed with the following restrictions:
1.
Users should be aware that personal use is still subject to all of
the rules in this policy including inspection and monitoring.
Personal use does not imply private use.
2.
There must be no cost to the county.
3.
Use must be conducted on the user’s own time. However, just as
personal telephone calls are permitted providing that they do not
interfere with an employee’s obligation to carry out their
assigned duties in a timely and effective manner, so shall
personal internet access and email be permitted.
4.
Use must not interfere with other employees performing their jobs
or undermine the use of county resources for official purposes.
5.
Use of county technology resources, such as the internet and
email, for operating a personal business is prohibited.
6.
Personal use of county resources by an employee neither expresses
nor implies sponsorship or endorsement by the county.
Acceptable Use
Acceptable internet and/or email activities are those that conform to
the purpose, goals, and mission of the County and to each user’s job
duties and responsibilities. The following list although not
all-inclusive, provides some illustrations of acceptable use.
1.
Communication and information exchange directly related to the
mission, charter or work tasks of the Polk County agency.
2.
Communications for the purpose of maintaining job knowledge and
skills or for professional development, this is not limited to but
includes education relevant to the User’s current job field and is
at the discretion of the User’s department head.
3.
Use in applying for or administering grants or contracts for
county government research programs or work related applications.
4.
Communications with state agencies, other counties and businesses
with which the county conducts business.
5.
Acceptable use must be legal, ethical, reflect honesty, and show
restraint in the consumption of shared resources.
Unacceptable Use
Unacceptable use can be defined generally as activities that do not
conform to the purpose, goals, and mission of the agency and to each
user’s job duties and responsibilities. Any Internet access or email
usage in which acceptable use is questionable should be avoided. The
user should never assume an activity is acceptable.
The following list, although not all-inclusive, provides some
illustrations of unacceptable uses:
1.
Use of email for any purpose that violates a federal, state, or
local law.
2.
Use for any for profit activities unless specific to the charter,
mission or duties of the Polk County Agency.
3.
Unauthorized non-profit business activities. This includes the
conducting of any non-governmental related fund raising or public
relations activities such as solicitation for religious and
political causes.
4.
The display of any kind of sexually explicit image or document on
any county system, which is also a violation of the county’s
sexual harassment policy. In addition, sexually explicit material
may not be archived, stored, distributed, edited, or recorded
using the county network or computing resources.
5.
The display of any derogatory racial or derogatory religious
content, political statements, offensive language or any material
that may negatively reflect on Polk County.
6.
Use of any county computing resources for illegal activity is
prohibited.
7.
No user may use county facilities knowingly to download or
distribute pirated software or data. This includes the burning or
saving of music or video off of file sharing applications.
8.
No user may modify or reconfigure their Internet web browser
connection options or email application account information
without prior approval from the Information Technology Department.
9.
Any user who attempts to disable, defeat, or circumvent any county
security facility will be subject to immediate termination of
Internet access and email service and subject to disciplinary
action.
10.
The user should not violate intellectual property rights
(copyright), information ownership rights, or system security
mechanisms.
11.
NO hate mail, NO harassment of any form, NO chain letters, NO
pornography, NO $$$$ opportunity letters.
12.
No free standing instant messaging programs. Stripped down
versions of Instant Messengers are acceptable (see personal use
section above). These will be taken on a case by case basis by the
IT Director. Approval must be obtained by the department head from
the IT Director before any Instant Messenger can be used.
13.
Continuous streaming radio and video is not acceptable. These
applications take up a lot of the internet connection causing
other users to slow down.
14.
The use of any encryption method not approved by the IT department
or otherwise mandated by a state agency is prohibited.
Training
All employees will be trained in the various aspects of this policy.
New employees will need to receive training before they are given
access to the network, Internet, or email. Department heads are
responsible for scheduling new employees for this training.
Monitoring
The IT department will monitor performance and security issues on an
on going basis and will only monitor internet access and email when
authorized by the IT director. This does not preclude incidental
access in the normal course of maintenance of the email system or the
network in general. However, since all activity using the internet or
email is the property of the County, the County may at any time
examine any messages or files on the system. No user should have any
expectation of privacy.
Security
Each user is responsible for all actions taken while using his/her
user profile, password, or access code. Therefore, none of these
should be shared with anyone else (including other employees of the
county, except the IT department). They must not be written down and
stored, posted anywhere, or stored on the computer system in an
unencrypted form.
The examination, modification, copying or deleting of files and/or
data belonging to other employees without their prior consent is
prohibited, except under the direction of the Department Head or
higher authority.
All users are responsible for the prevention of the spread of viruses.
Any file, program or document received on media (diskettes, CD-Rom, or
tapes), through the internet (including email) or through file
transfer must be checked for viruses immediately thereby eliminating
the possibility of infecting the County’s entire network. The IT
department will provide anti-virus software for every computer and
server.
The internet provides easy access to software distributed by companies
on a trial basis. The free access does not indicate that the software
is free or that it may be distributed freely. Applicable software
copyright laws must be followed. In addition, software may not be
loaded onto any county computer system, through any of the above
methods, without prior approval from the IT director. This includes
shareware, freeware, personal software, or internet distributed
programs.
Modems shall not be added to any networked computer system without
prior approval from the IT Director. Modems provide a backdoor to the
county network, which creates significant vulnerability to security
threats. Additionally, no home or personal computers will be allowed
on the County Network or in county office space. Personal or home
computers cannot be guaranteed virus or spy-ware free and thus pose a
significant threat to the county network. Possibly infected media
transferred from one machine to another is a potential threat to the
county network and must be avoided at all costs.
Retention of Email
Employees should be aware that when they have deleted a message from
their workstation mailbox it might not have been deleted form the
central mail system. The message may be residing in either the sender
or receiver’s mailbox or forwarded to other recipients. Furthermore,
the message may be stored on any of the aforementioned back-ups for an
indefinite period. Note that email has been classified as “public”
documents, which should be kept in mind when you create or store
email. Users should delete email messages as soon as possible after
reading. An accumulation of files will degrade system performance and
response times.
Enforcement and Violations
Violation of this policy may result in termination of Internet Access
or email services, possible disciplinary action, up to and including
dismissal and criminal charges where appropriate. Termination of
services may be at the request or determination of the department
head, IT director, or higher authority. Any disciplinary action will
be in accordance with the Polk County Personnel Policy.
Written Agreement Required
The county will require employees to read and signify acceptance of
the terms of this
policy by signing the following “Understanding of Policy” before
making Internet Access
or email service available.
Signature ____________________ Date_______________
 3 D EPARTAMENTO JURIDICO K5203(381)2006 ORD Nº 3438060
3 D EPARTAMENTO JURIDICO K5203(381)2006 ORD Nº 3438060 NA KRASU CELO POLETJE KRASPASS DEGUSTACIJE IN DOŽIVETJA VEČ
NA KRASU CELO POLETJE KRASPASS DEGUSTACIJE IN DOŽIVETJA VEČ INFORMATION ABOUT THE EXPERT PATIENT PROGRAMME THE EXPERT PATIENT
INFORMATION ABOUT THE EXPERT PATIENT PROGRAMME THE EXPERT PATIENT 20121213 BEMANNING 2013 STUGVÄRDAR PROGRAM STUGFOGDAR VECKA (MÅSÖ) MÅNAD
20121213 BEMANNING 2013 STUGVÄRDAR PROGRAM STUGFOGDAR VECKA (MÅSÖ) MÅNAD POSTĘPOWANIE A12021114712MR ZAŁĄCZNIK NR 10 DO SIWZ SPECYFIKACJA WYKONANIA
POSTĘPOWANIE A12021114712MR ZAŁĄCZNIK NR 10 DO SIWZ SPECYFIKACJA WYKONANIA APORTES DE LA COOPERACIÓN ESPAÑOLA PARA HABITAT III BUENAS
APORTES DE LA COOPERACIÓN ESPAÑOLA PARA HABITAT III BUENAS ДЕРГАЧІВСЬКА МІСЬКА РАДА ВИКОНАВЧИЙ КОМІТЕТ РІШЕННЯ ВІД 12 ВЕРЕСНЯ
ДЕРГАЧІВСЬКА МІСЬКА РАДА ВИКОНАВЧИЙ КОМІТЕТ РІШЕННЯ ВІД 12 ВЕРЕСНЯ S ERVIZO DE RELACIÓNS EXTERIORES COLEXIO DE SAN XEROME
S ERVIZO DE RELACIÓNS EXTERIORES COLEXIO DE SAN XEROME COMUNICADO 023 MARCELO EBRARD CONCLUYE VISITA DE TRABAJO A
COMUNICADO 023 MARCELO EBRARD CONCLUYE VISITA DE TRABAJO A VERS DES ENTITÉS PLUS STABLES (CHAPITRE 6 DU
VERS DES ENTITÉS PLUS STABLES (CHAPITRE 6 DU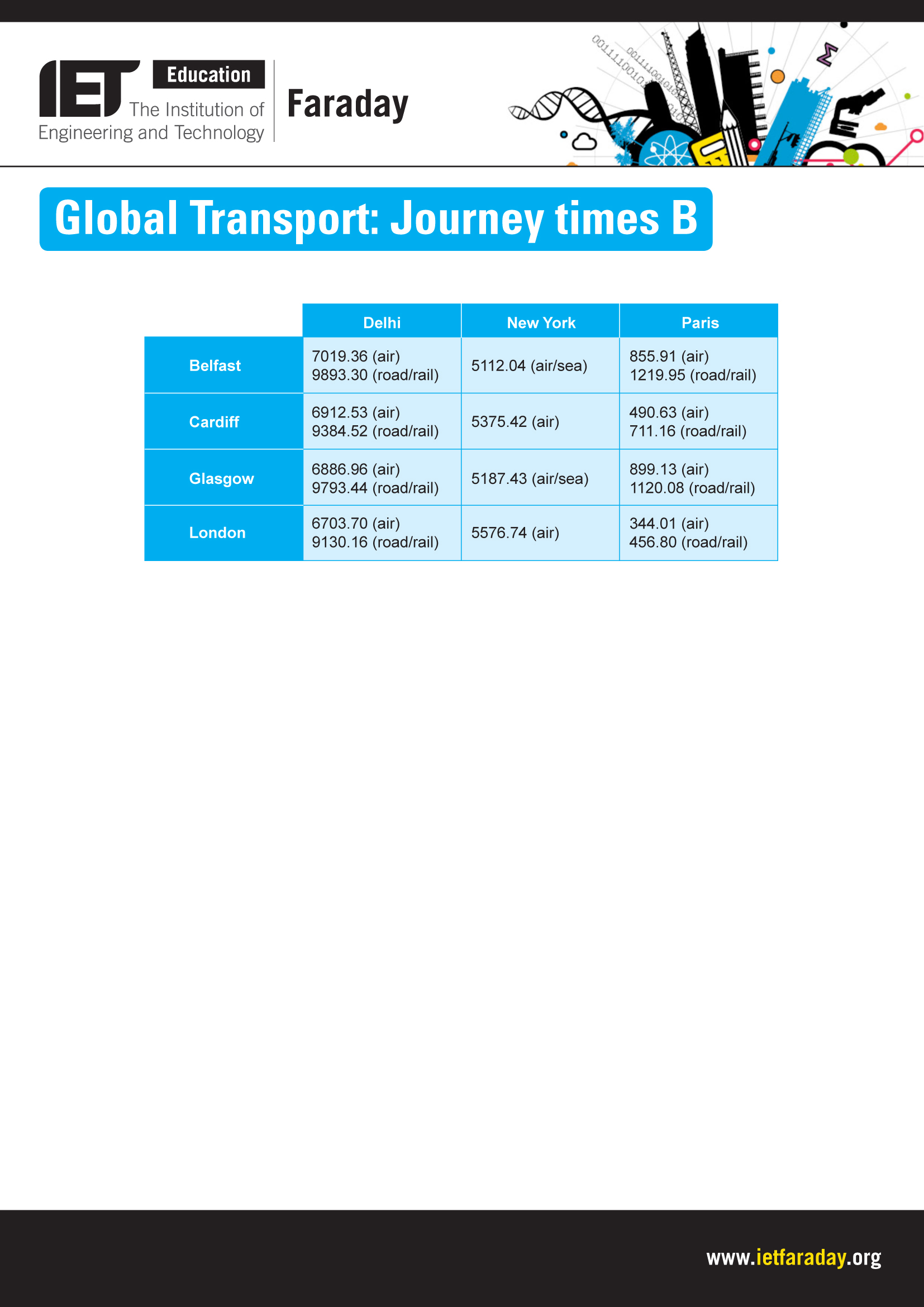 THE TABLE ABOVE SHOWS THE DISTANCES BETWEEN CITIES IN
THE TABLE ABOVE SHOWS THE DISTANCES BETWEEN CITIES IN Z USATZINFORMATIONEN ZUR KATASTROPHENSCHUTZÜBUNG ALLGEMEINE INFOS ZUR ÜBUNG DIE
Z USATZINFORMATIONEN ZUR KATASTROPHENSCHUTZÜBUNG ALLGEMEINE INFOS ZUR ÜBUNG DIE WWWRESUMOSCONCURSOSHPGCOMBR RESUMO TRABALHISTAREMUNERAÇÃO AUTOR CLEONICE NEVES (CFJNEVESYAHOOCOMBR ) REMUNERAÇÃO
WWWRESUMOSCONCURSOSHPGCOMBR RESUMO TRABALHISTAREMUNERAÇÃO AUTOR CLEONICE NEVES (CFJNEVESYAHOOCOMBR ) REMUNERAÇÃO